Why choose Serenety ?
-
1
Identify the threats and risks related to your exposure on the web
-
2
Detect vulnerabilities and data leaks before they are exploited by attackers
-
3
Maintain an up-to-date map of your exposed perimeter
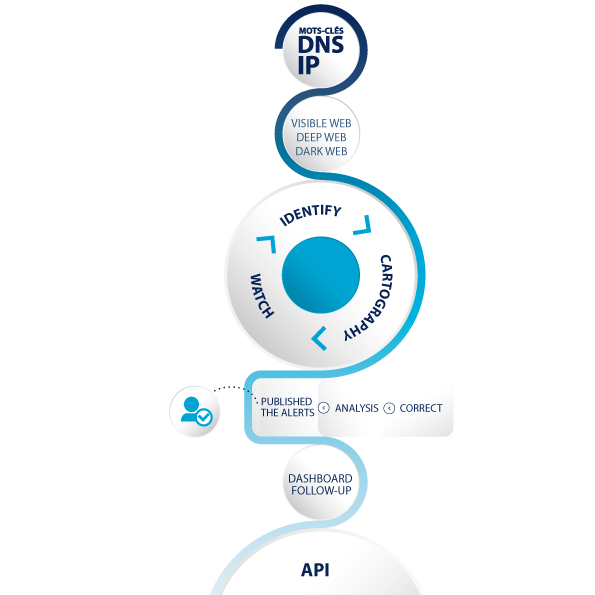
Cyber Threat Intelligence according to XMCO
2 axes to be one step ahead of your attackers
-
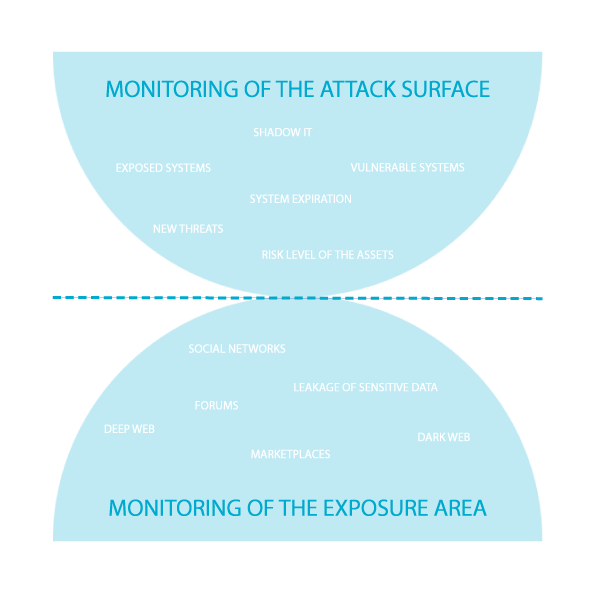
Attack surface
• Global mapping of your perimeter
• Monitoring of assets and identification of existing vulnerabilities
• Tracking changes and obsolescence of assets -
Exhibition surface
• Tracking your exposure to known vulnerabilities
• ShadowIT: Perimeter updated with each new detection of an asset outside the perimeter
• Monitoring of future attack campaigns on social networks, the Deep Web and the Dark Web

Serenety monitors the 3 layers of the web
To identify your vulnerable or sensitive assets, your exposed data and the threats that target you
-
The clear web
General search engines (Google, Bing, Duckduckgo, etc.) and sites with an integrated search engine (Github, Twitter, etc.)
-
The deep web
Discussion forums, social networks, blogs and other content requiring specific access.
-
The dark web
Tor and I2P sites, attacker forums, marketplaces where stolen data is resold, ransomware operator sites and all the spaces where cybercriminals exchange (Telegram, Discord, etc.).

Watch the video
Map your assets and track your exposure
Serenety scans the web and automatically correlates the results from our scans and manual analyzes using:
-
OSINT methodology
• Research, Collection and Analysis of information in open sources
• Using techniques and tactics known to attackers to identify targets and develop new resources to enable attacks -
40 detection module
• Monitoring of the attack surface: Identification of exposed or vulnerable systems, Shadow IT (unvalidated/authorized websites), the level of risk of your assets (presence on Phishing sites, on blacklists, etc.) , new threats on your perimeter (0day breaches), monitoring of the obsolescence and expiration of your systems
• Exposure surface monitoring: Monitoring of social networks and forums or marketplaces on the deep and dark web, identification of sensitive or critical data leaks for your organization -
Watch and analysis teams
• Our team is made up of profiles graduates of major engineering schools or specialized in economic intelligence
• Our team is CERT certified
Concrete feedback and strategic analyzes
We analyze feedback from our automated controls as well as attack trends.
-
0 false positives
Qualified and contextualized alerts without false positives.
-
Managerial syntheses
Adapted to your needs to follow the evolution of your threats and your levels of risk.
-
Actions plans facilitating remediation
Benefit from recommendations in each of the qualified alerts.
-
A safety modes
Statistics and a security score to assess your overall level of security.
-
Analytics notes on attacker groupes and their operating modes
We frame our analyzes by making the link with the PRE matrix of the MITER ATT&CK framework. We track attack trends and analyze changing criminal modus operandi
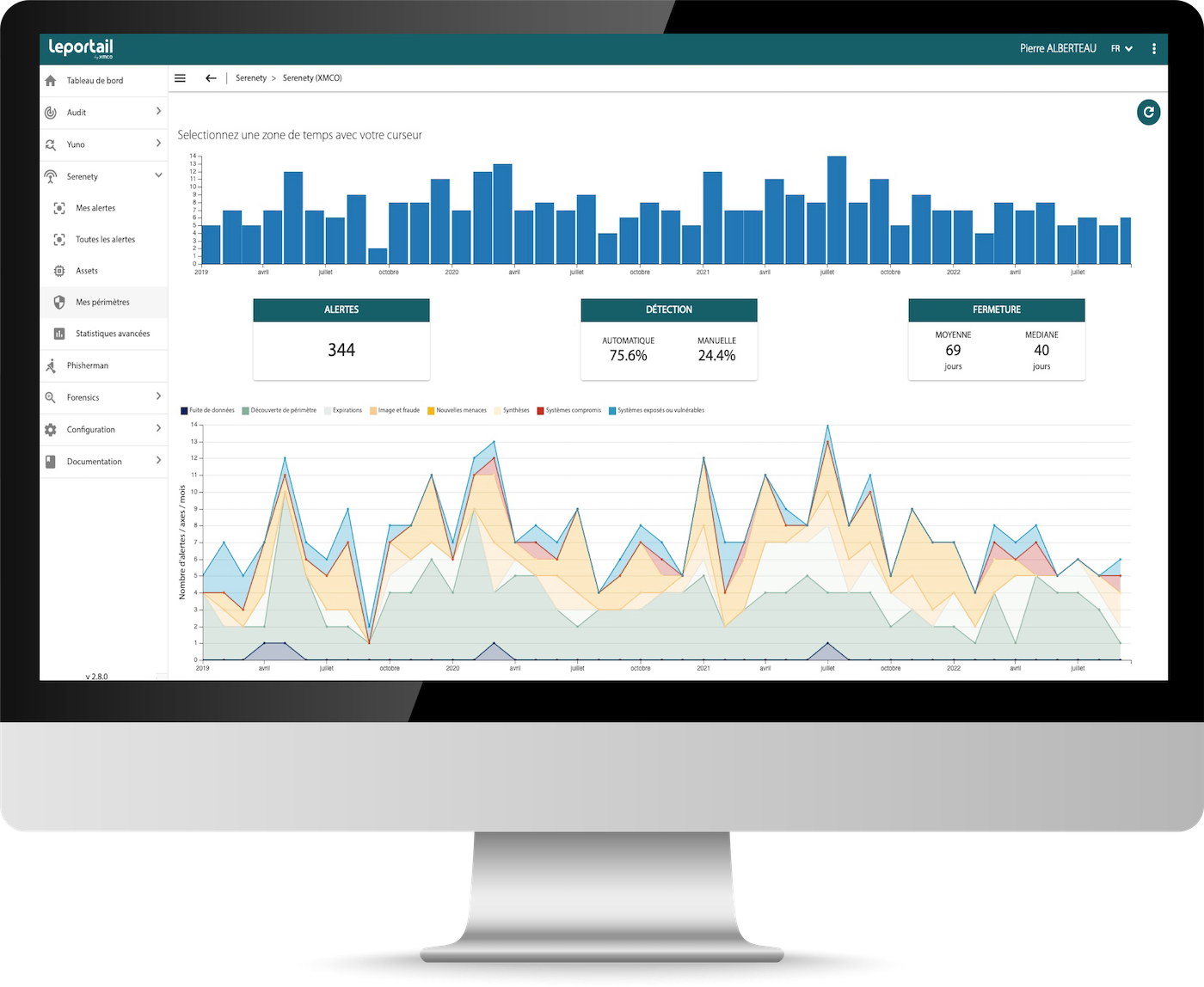
The use of Serenety is non-intrusive and does not require the installation of probes or the collection of logs.
A secure API and web portal are available to follow up on alerts with our team.
-
1
The Portal, an ergonomic solution, accessible in SaaS.
-
2
Your alerts, security statistics and your action plans: all your information in one place.
-
3
You monitor your perimeter and its permanent enrichment on a daily basis.
-
4
The API that allows you to export your alerts directly into your internal tools.
The covered risks
You are in safe hands
XMCO supports nearly 300 companies each year.








