The cyber context of SMEs in France
Often more vulnerable than large accounts, SMEs are increasingly targeted by cyberattacks.
And for good reason, a study by Hiscax Insurance indicates that between 2017 and 2018, the evolution of the number of SMEs victims of a cyber incident increased from 36% to 63%.
The protection of SMEs is made difficult in particular because of aggravating circumstances:
Our engagements
The security audit is one of the solutions to identify the main vulnerabilities of your information system, and to define the overall level of security. This analysis allows you to quickly orient your cybersecurity strategy.
-
An offer 100% in line with the needs and business context of SMEs.
-
A fixed rate, adapted to the budgets of SMEs.
-
A clear dashboard of your security.
-
A checklist of vulnerabilities and associated recommendations.
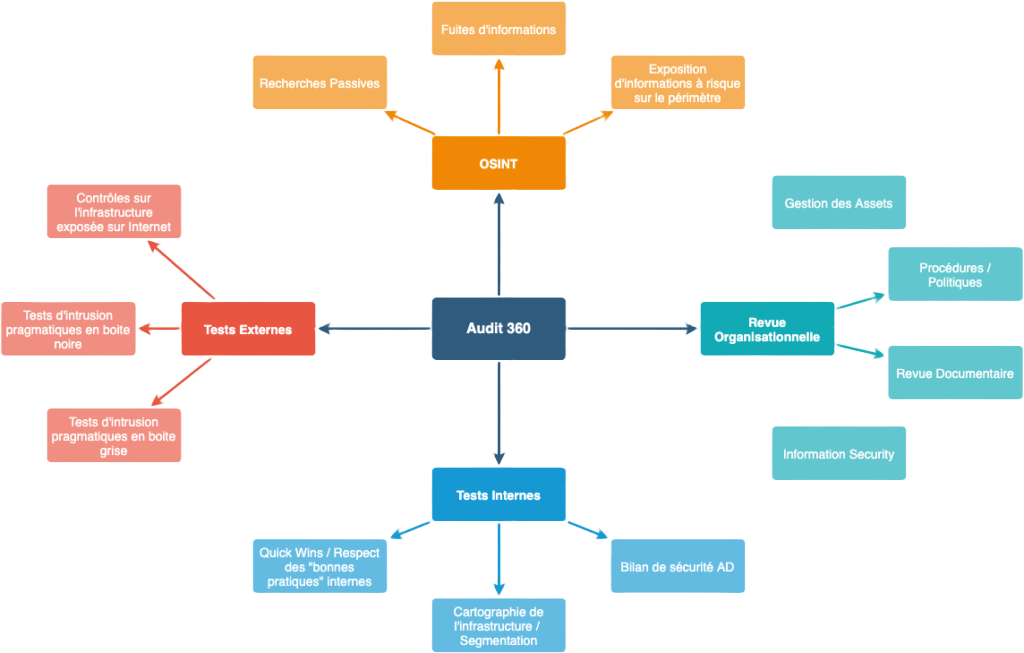
Our methodology
-
Passive Research / Open Source Intelligence (OSINT)
Research and analysis of information related to the company in the various sources of public information present on the “Internet” that may affect the security of the company, its data, its employees or facilitate the implementation of attack scenarios (employees, financial data, business/technical documents, secrets, etc.).
We rely in particular on search engines (Google, DuckDuckGo, Yandex, Bing, etc.), information exchange or code deposit platforms (Stack Overflow, Reddit, GitHub, etc.), social networks , information from DNS resolvers, specialized forums, etc. -
External Intrusion Tests (EIT)
We are evaluating here the ability of an “external” attacker to compromise or harm the Information System from the Internet. These tests in the 360 context are generally carried out in a “**black box**” (without a user account) (showcase site, extranet, business application).
However, we can target critical “grey box” applications (with user accounts communicated by the technical teams) in order to delve into more complex scenarios according to the needs of each client. -
Internal Intrusion Tests (ITI)
Technical audit of the Information System from internal access (on premises or via VPN). We assess the ability to compromise or harm the client’s Information System by an attacker with internal access, a collaborator or a malicious service provider.
The usual objective is to take total control of resources (e.g. by taking control of a domain administrator account in an Active Directory context) or highlighting so-called “risky” information recovery scenarios (approach via “flags” to be retrieved set out upstream of the audit). -
Wi-Fi Audit
The goal is to simulate the behavior of an attacker able to interact with the company’s Wi-Fi access in order to highlight exploitable vulnerabilities near the premises.
-
Evaluation of the main cloud services used
Here we evaluate the attack surface of the environment administered by the customer (or by outsourcers) and carry out various checks on the configuration (generally with an administration account with read-only rights).
-
Environment maturity audit
Whether it is directly administered by the client or by various outsourcers, we will carry out a **pragmatic** study of the procedures and policies put in place, the documents available, etc. (organizational audit approach).
The objective here is to understand the practices in force within the company, to identify its issues and then to assess the level of maturity of the company with regard to its needs and the market (good practices and average level observed within comparable organizations) in order to produce an inventory supplemented by one or more interviews. -
Raising employee awareness of cyber-security risks
Depending on the request and the context of each client, we will make the choice to:
– a full-scale awareness-raising exercise in order to take stock of the level of employee awareness (fictitious phishing campaign with a model);
– an awareness-raising workshop presented by XMCO consultants around the theme of “general safety” in order to help all technical and non-technical employees to better understand the risks.
Why choose XMCO?
-
We are PASSI qualified by ANSSI.
-
XMCO is an official CERT. Any vulnerability detected is immediately integrated into the tests in progress.
-
20 years of experience in auditing and penetration testing.
-
Additional options to go further: Phishing, Audit active directory…

